

reposting my comment from the thread yesterday:
reposting my comment in a thread last month about this:
in b4 haveibeenhaveibeenflocked.
they have a list of their current collection of 239 .csv files but sadly don’t appear to let you actually download them to query offline
they now have 519 sources, some of which are downloadable from muckrock but many aren’t.
i still don’t understand why this website isn’t open source and open data, and i strongly recommend thinking carefully about it (eg, thinking about if you’d mind if the existence of your query becomes known to police and/or the public) before deciding if you want to type a given plate number in to it.









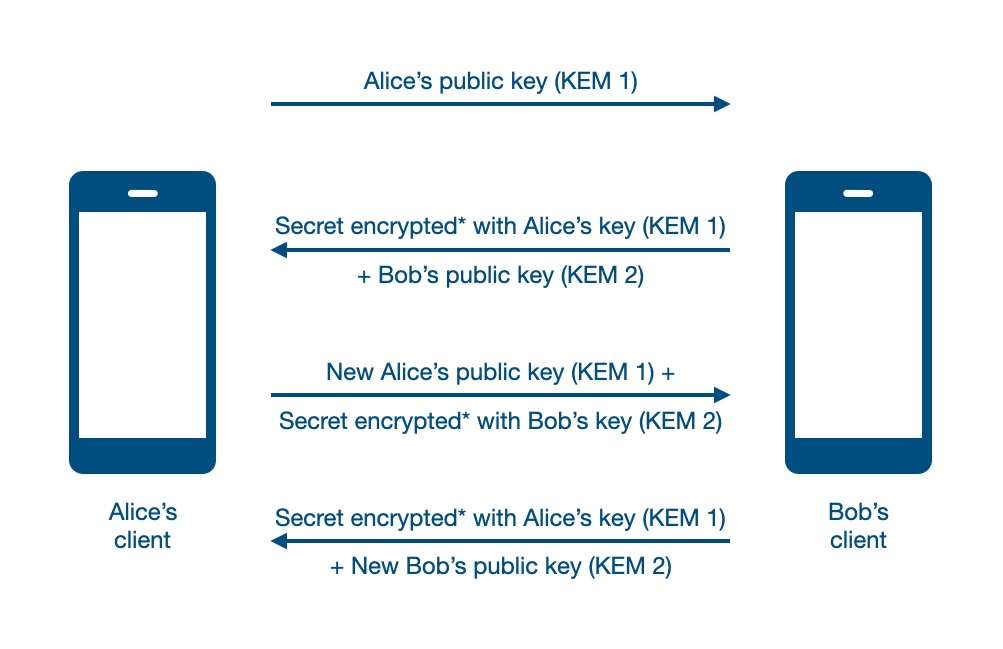


the fact that they know your plate number is different than knowing if you (or someone) queried a website about which police queried flock about it