

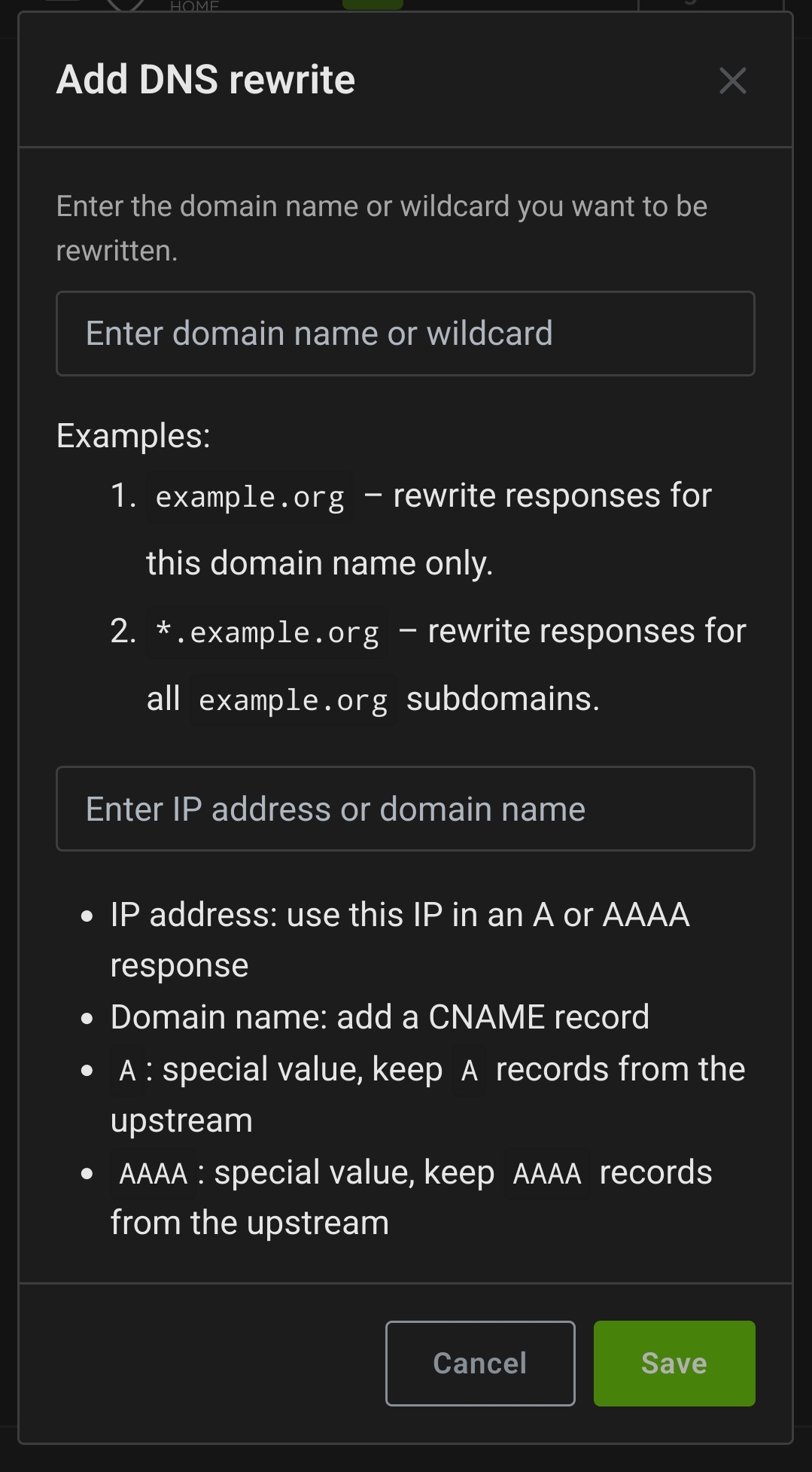
You don’t need 2 reverse proxies as others have said. What I did is just add a DNS rewrite entry in my adguardhome instance to point my domain.tld to the LAN IP of my reverse proxy.


You don’t need 2 reverse proxies as others have said. What I did is just add a DNS rewrite entry in my adguardhome instance to point my domain.tld to the LAN IP of my reverse proxy.


I use some generic names.


Yeah obsidian’s pretty nice. I use the daily notes feature built into it for my journal.


I ran a podman quadlet setup as a test some time ago. My setup was a little like this:
If you create a new network in podman you can access other containers and pods in the same network with their name like so container_name:port or pod_name:port. This functionality is disabled in the default network by default. This works at least in the newer versions last I tried, so I have no idea about older podman versions.
For auto-updates just add this in your .container file under [] section:
[Container]
AutoUpdate=registry
Now there’s two main ways you can choose to update:
podman-auto-update.timer to enable periodic updates similar to watchtowerpodman auto-update manually# Check for updates
podman auto-update --dry-run
# Update containers
podman auto-update
If you run adguard home it’s pretty easy. Just add a DNS rewrite to your local IP.
How are you running nginx and immich exactly? With containers or on the host?
I don’t know nixos that much but that looks like nixos configuration to me, so it’s running on the host I assume?


Some feeds I follow


Obsidian with syncthing for syncing between my phone and PC.


For Tailscale you can disable key expiry on select devices.


I use traefik with a wildcard domain pointing to a Tailscale IP for services I don’t want to be public. For the services I want to be publicly available I use cloudflare tunnels.


I think you have a misunderstanding. Restic and Borg checks the integrity of the backup repository and not the files being backed up.


i call it “butter FS”


Yeah quadlets are pretty cool. I have them organized into folders for each pod. podman auto-update is also another pretty nice feature. I don’t use the systemd timer for auto-update. Instead I just do podman auto-update --dry-run to check for updates and update my quadlet files and configs if any changes are required then I run the updates with podman auto-update.


podman-generate-systemd is outdated. The currently supported way to run podman containers using systemd services would be Quadlet files.
https://docs.podman.io/en/latest/markdown/podman-systemd.unit.5.html
Edit: I just saw that you use debian so idk if Quadlets are a thing with the podman version on debian.


Any reason why you use compose and not quadlets?


Do you mean networking between them? There’s two ways of networking between containers. One of them is to create a custom network for a set of containers that you want to connect between each other. Then you can access other containers in that network using their name and port number like so
container_name:1234
Note: DNS is disabled in the default network by default so you can’t access other containers by their name if using it. You need to create a new network for it to work.
Another way is to group them together with a pod. Then you can access other services in that same pod using localhost like so
localhost:1234
Personally in my current setup I’m using both pods and seperate networks for each of them. The reason is I use traefik and I don’t want all of my containers in a single network along with traefik. So I just made a seperate network for each of my pods and give traefik access to that network. As an example here’s my komga setup:
I have komga and komf running in a single pod with a network called komga assigned to the pod. So now I can communicate between komga and komf using localhost. I also added traefik to the komga network so that I can reverse proxy my komga instance.


NewPipe on my phone. I don’t have PC I can use rn but when I used to have one I’d just use my browser (mainly Firefox) with ublock origin to watch YouTube (without signing in).
Do you actually need to move the admin ui off of port 80/443 if you are just forwarding ports? I don’t think you need to. That said I actually don’t know much about port forwarding since I use Tailscale because of CGNAT.
My understanding of port forwarding is that you are forwarding connections to your WAN IP/port to a LAN IP/port. Since the router admin ui is available only on LAN by default, you don’t need to change it’s port from 80/443.